Smart Building Network Resilience
Understanding the Importance of Layered Security
Modern smart buildings demand robust security frameworks that go beyond single-point solutions. The concept of layered security mirrors medieval castle defenses - where multiple barriers create cumulative protection. When one barrier fails, others remain intact to safeguard critical systems. This philosophy proves particularly vital as building networks grow more interconnected and complex.
Consider how financial institutions protect assets: vaults sit behind guarded doors, monitored by cameras, with alarms and time-delay mechanisms. Similarly, smart infrastructure requires tiered protections - from physical barriers to digital firewalls - creating overlapping security zones that deter both physical intruders and cyber threats.
Physical Security Measures
The foundation of any security strategy begins with controlling physical access. Modern facilities employ sophisticated methods beyond traditional locks and keys:
- Biometric scanners that verify unique physiological characteristics
- Tailgating detection systems that prevent unauthorized piggybacking
- AI-powered surveillance that identifies unusual behavior patterns
Server rooms and network hubs require particularly stringent controls, often implementing dual-authentication protocols where two separate credentials must be presented simultaneously. Regular security drills and random equipment audits further reinforce physical protections.
Network Segmentation and Isolation
Modern network architecture follows the principle of compartmentalization, similar to submarine bulkheads that contain flooding. By dividing networks into isolated segments:
- HVAC controls operate on separate channels from security systems
- Lighting networks remain distinct from data transmission pathways
- Building automation functions in its own protected environment
This approach limits potential damage from breaches, as attackers gaining access to one segment find themselves contained within that digital compartment. Proper segmentation requires careful planning to balance security with operational efficiency.
Data Encryption and Access Control
In today's threat landscape, data protection demands military-grade encryption standards. Modern systems employ:
- End-to-end encryption for all data transmissions
- Quantum-resistant algorithms for future-proofing
- Dynamic key rotation to prevent decryption attempts
Access management follows the principle of least privilege, where users receive only the permissions absolutely necessary for their roles. Regular permission audits ensure this principle remains enforced as staff responsibilities evolve.
Regular Security Audits and Penetration Testing
Proactive security requires continuous evaluation through:
- White-hat hacking simulations that mimic real-world attack vectors
- Vulnerability scanning that identifies potential weaknesses
- Red team exercises that test organizational response protocols
These assessments should occur on both scheduled and surprise bases, with findings meticulously documented and addressed. The most secure facilities maintain bug bounty programs that incentivize external researchers to report vulnerabilities.
Employee Training and Awareness
Human factors represent both the weakest link and strongest defense in security systems. Effective training programs incorporate:
- Simulated phishing campaigns with real-time feedback
- Gamified learning modules that reinforce best practices
- Behavioral analytics that identify risky patterns
Security-conscious cultures develop when staff understand not just procedures, but the reasoning behind them. Regular tabletop exercises help teams practice responding to various breach scenarios.
Redundancy and Failover Mechanisms: Ensuring Continuous Operation
Redundancy in Critical Systems
Mission-critical operations cannot rely on single points of failure. Modern redundancy strategies often employ:
- Active-active configurations where multiple systems share loads
- Geographically dispersed backups that survive regional disasters
- Diverse infrastructure providers to prevent vendor-specific failures
The financial sector provides excellent examples, where trading systems maintain multiple parallel data centers that can instantly assume primary roles during outages.
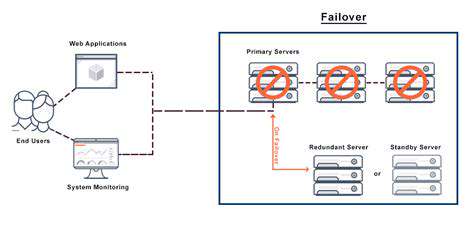
Failover Mechanisms
Seamless transition during failures requires sophisticated failover protocols:
| Failover Type | Implementation | Recovery Time |
|---|---|---|
| Hot standby | Fully mirrored systems | Seconds |
| Warm standby | Pre-configured backups | Minutes |
| Cold standby | Basic infrastructure | Hours |
The choice between these approaches depends on both technical requirements and cost-benefit analysis.
Types of Redundancy
Modern systems implement redundancy at multiple levels:
- Hardware: Duplicate servers with automatic failover
- Network: Multiple internet providers with automatic switching
- Data: Real-time replication across storage arrays
- Power: Backup generators with automatic transfer switches
Cloud architectures have revolutionized redundancy strategies, allowing organizations to leverage globally distributed infrastructure with minimal capital investment.
Implementing Redundancy Strategies
Effective implementation follows these phases:
- Criticality assessment of all systems
- Failure mode analysis for each component
- Redundancy design matching business requirements
- Comprehensive testing under realistic conditions
Testing must include simulated component failures during peak loads to verify systems perform as intended under stress.
Monitoring and Maintenance
Redundant systems require vigilant oversight through:
- Automated health checks that verify all components
- Predictive analytics that forecast potential failures
- Scheduled maintenance that refreshes aging equipment
Modern monitoring solutions use machine learning to establish normal patterns and flag anomalies before they cause disruptions.
Cost Considerations
While redundancy represents additional expense, the calculus changes when considering:
- Revenue losses during downtime
- Reputation damage from service interruptions
- Regulatory penalties for availability failures
For many organizations, the cost of redundancy proves far lower than the risk of going without.
Security Implications of Redundancy
Redundant systems introduce unique security challenges:
- Each additional component expands the attack surface
- Synchronization between systems can create vulnerabilities
- Backup systems often receive less security scrutiny
Security teams must apply equal protection to primary and backup systems alike.
Effective gamification requires careful integration with learning objectives rather than superficial game elements. For example, language programs might implement progress tracking similar to role-playing games, where students level up their vocabulary skills through demonstrated mastery rather than simply playing word-matching games.
Data Integrity and Backup Protocols: Safeguarding Critical Information

Ensuring Data Accuracy
Data quality initiatives employ multiple verification layers:
- Input validation that prevents incorrect data entry
- Automated consistency checks across related datasets
- Statistical analysis that identifies anomalous values
Financial institutions provide models for data integrity, where reconciliation processes compare multiple independent records to detect discrepancies.
Backup Procedures for Data Recovery
Modern backup strategies follow the 3-2-1 rule:
- 3 total copies of important data
- 2 different storage media types
- 1 offsite copy
Cloud solutions now enable more sophisticated approaches like continuous data protection, where every change gets recorded and can be restored to any point in time.
Data Validation and Verification Processes
Validation occurs at multiple stages:
| Stage | Techniques | Purpose |
|---|---|---|
| Entry | Format checking, range validation | Prevent incorrect data |
| Processing | Cross-system reconciliation | Ensure consistency |
| Output | Statistical analysis, sampling | Verify results |
Automated validation scripts should run continuously rather than relying solely on periodic manual reviews.
Data Security and Access Controls
Modern access management incorporates:
- Role-based permissions with time-bound access
- Behavior-based authentication that adapts to usage patterns
- Blockchain-based audit trails for critical changes
The principle of separation of duties ensures no single individual can compromise data integrity.
Disaster Recovery Planning
Effective disaster recovery requires:
- Clearly defined recovery time objectives
- Documented escalation procedures
- Regular scenario testing with all stakeholders
Plans must address both technical restoration and business process continuity.
Read more about Smart Building Network Resilience
Hot Recommendations
- AI in Property Marketing: Virtual Tours and VR
- Water Management Solutions for Sustainable Real Estate
- IoT Solutions for Smart Building Energy Management
- Sustainable Real Estate: Building a Greener Tomorrow
- Sustainable Real Estate: From Concept to Community
- AI Driven Due Diligence for Large Scale Developments
- Real Estate Sector and Global Climate Agreements
- Smart Buildings: The Key to Smarter Property Management
- Zero Waste Buildings: A Sustainable Real Estate Goal
- Understanding Climate Risk in Real Estate Financing