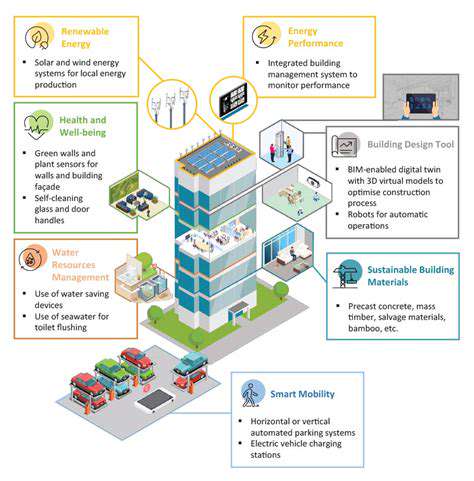
AI for Personalized Tenant Services
Implementing a Predictive Maintenance Program
Transitioning to predictive maintenance resembles implementing a new business process rather than just adopting technology. The most successful implementations begin with pilot projects targeting high-value, failure-prone equipment, allowing teams to demonstrate quick wins while building organizational buy-in.
Effective programs combine multiple data streams - vibration analysis, thermal imaging, oil analysis - to create comprehensive equipment health profiles. Maintenance managers report that the biggest challenge isn't collecting data, but transforming it into clear maintenance directives that technicians can act upon.
Training programs should focus equally on data interpretation and cultural change. Technicians need to understand not just how to use new tools, but why their maintenance approach must evolve. Regular review sessions help teams refine their predictive models based on actual equipment performance and failure patterns.
Streamlined Lease Management and Financial Processes
Streamlined Lease Administration
Modern lease management solutions have evolved far beyond simple calendar reminders. Today's systems act as centralized command centers for all lease-related activities, automatically tracking critical dates, payment schedules, and compliance requirements across entire real estate portfolios.
The automation of routine tasks creates unexpected benefits - finance teams gain hours previously spent manually tracking lease documents, while legal departments appreciate automated alerts for upcoming renewals and option periods. This operational efficiency translates directly to bottom-line improvements through better lease terms and reduced administrative costs.
Financial Reporting and Analysis
Advanced lease accounting tools now provide CFOs with unprecedented visibility into long-term liabilities. Real-time dashboards transform complex lease portfolios into clear financial pictures, showing exactly how current commitments affect future cash flows and balance sheets.
Forward-thinking organizations use this data to optimize their real estate strategies, identifying underutilized spaces and renegotiating terms well before renewal deadlines. The financial impact often surprises executives - what begins as a compliance project frequently uncovers significant cost-saving opportunities.
Compliance and Risk Management
Lease accounting standards continue evolving, creating compliance challenges for organizations managing large portfolios. Automated systems now handle the heavy lifting of compliance tracking, ensuring proper classification and reporting without manual intervention.
Risk management benefits extend beyond accounting compliance. Centralized systems flag unusual clauses, track landlord performance, and monitor market conditions - all factors that could impact portfolio performance. This holistic view helps organizations anticipate problems before they become costly issues.
Improved Decision-Making and Growth
The most strategic organizations treat lease data as a competitive advantage, using historical performance metrics to inform expansion plans and portfolio optimization. When combined with market analytics, lease data helps identify ideal locations, negotiate better terms, and time market entries perfectly.
Growth-focused companies leverage these insights to develop flexible real estate strategies that support both short-term needs and long-term visions. The ability to model various scenarios gives executives confidence in their real estate decisions, knowing they're backed by comprehensive data rather than gut instinct.
Enhanced Security and Fraud Detection
Robust Authentication Protocols
In today's threat landscape, basic password protection no longer suffices. Modern authentication resembles a multi-layered security checkpoint, combining device recognition, behavioral biometrics, and contextual analysis to verify user identities.
The most effective systems now incorporate invisible authentication measures that don't burden legitimate users while creating significant obstacles for attackers. Continuous authentication monitors user behavior throughout sessions, not just at login, providing ongoing protection against account takeovers.
Advanced Fraud Detection Algorithms
Cutting-edge fraud prevention now resembles a sophisticated game of chess against attackers. Machine learning models don't just look for known fraud patterns - they identify emerging threats by detecting subtle anomalies in user behavior and transaction patterns.
The most successful implementations combine multiple detection methods: rules-based systems catch obvious fraud, while AI models uncover sophisticated schemes. This layered approach creates a security net that adapts as quickly as fraudsters evolve their tactics.
Data Encryption and Secure Storage
Data protection has moved beyond simple encryption at rest and in transit. Leading organizations now implement encryption that follows data wherever it travels, including through memory and during processing. This encryption everywhere approach minimizes exposure points throughout the data lifecycle.
Secure storage solutions have similarly evolved, with some systems now capable of performing computations on encrypted data without ever decrypting it. This breakthrough technology allows sensitive information to remain protected even during active use.
Continuous Monitoring and Alert Systems
Modern security operations centers function like air traffic control for digital assets. Advanced correlation engines analyze millions of events per second, separating true threats from background noise with remarkable accuracy.
The most effective systems now incorporate automated response capabilities that can contain threats in milliseconds - far faster than human operators could react. This combination of AI-driven detection and automated response creates a security posture that's both proactive and resilient.