Sea Level Rise Adaptation for Coastal Development
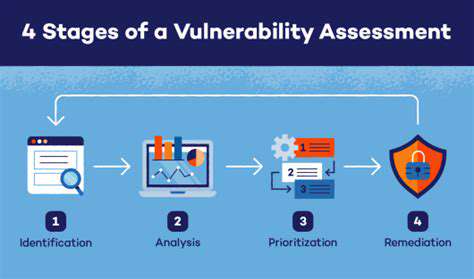
Understanding the Scope of Vulnerability Assessment
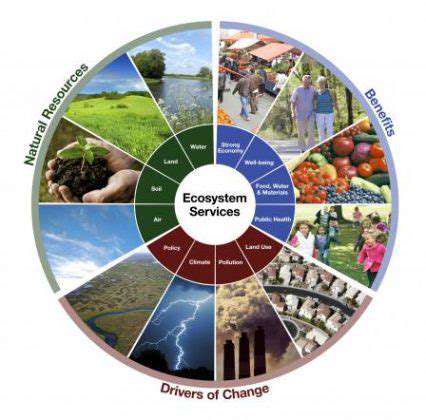
Every organization must recognize that vulnerability assessments form the backbone of robust information security. These evaluations meticulously pinpoint weaknesses across systems, networks, and applications. Security teams examine everything from software configurations to network architecture, creating a comprehensive security profile. Without thorough vulnerability assessments, organizations remain blind to risks that malicious actors could exploit at any moment. This proactive stance proves far superior to costly reactive measures after breaches occur.
The assessment's scope demands careful definition based on business-critical assets and regulatory landscapes. Teams must consider which systems would cause maximum disruption if compromised. Proper scoping ensures assessments deliver precise, actionable intelligence rather than overwhelming teams with irrelevant data. This focused approach enables security leaders to allocate resources effectively when implementing remediation.
Methods and Techniques for Vulnerability Identification
Modern security teams employ diverse vulnerability detection methods. Automated scanners efficiently flag known software vulnerabilities while penetration testers simulate sophisticated attacks. The most effective programs combine both approaches for complete coverage.
While automated tools excel at rapid scanning, they can't replicate human intuition. Seasoned security professionals often uncover system flaws that evade automated detection through manual testing techniques. Organizations must balance assessment depth with available resources, selecting methods that align with their risk profile and operational constraints.
Prioritizing and Reporting Findings
Not all vulnerabilities warrant equal attention. Effective prioritization considers exploit likelihood, potential damage, and business impact. This triage process ensures teams address critical risks immediately while scheduling less urgent fixes appropriately.
Clear reporting transforms technical findings into executive-level insights. Reports should detail vulnerabilities with severity ratings, business implications, and remediation timelines. Well-structured reports bridge the gap between technical teams and decision-makers, enabling informed security investments. They also provide audit trails demonstrating compliance with security frameworks.
Remediation and Mitigation Strategies
Vulnerability resolution requires pragmatic solutions balancing security and operations. Options range from immediate patches to architectural changes, each evaluated for cost and effectiveness. The best remediation plans address root causes while minimizing system downtime and user disruption.
When immediate fixes aren't feasible, mitigation controls reduce risk exposure. Temporary measures like access restrictions or monitoring rules can effectively neutralize threats until permanent solutions deploy. This layered approach maintains security posture during complex remediation projects.
Nature-Based Solutions: Utilizing Coastal Ecosystems
Coastal Wetlands: Nature's First Line of Defense
Coastal wetlands serve as dynamic barriers against climate change impacts. These ecosystems, including salt marshes and mangroves, absorb storm energy while preventing shoreline erosion. Their complex root systems stabilize sediment and nurture marine biodiversity. Protecting these natural defenses becomes increasingly vital as sea levels rise.
Beyond physical protection, wetlands function as carbon sinks. Their organic-rich soils sequester atmospheric carbon at remarkable rates. This dual functionality makes wetland conservation essential for both coastal resilience and climate mitigation efforts. Restoration projects demonstrate how nature-based solutions can outperform engineered alternatives in cost and sustainability.
Protecting and Restoring Mangrove Forests
Mangroves represent nature's sophisticated coastal engineering. Their intricate root networks dissipate wave energy while trapping sediment that builds land area. These ecosystems support fisheries and ecotourism, delivering economic benefits alongside environmental protection.
Successful mangrove conservation requires community engagement. Local knowledge combined with scientific research yields restoration techniques tailored to regional conditions. Investments in mangrove preservation generate long-term returns through disaster risk reduction and sustainable livelihoods.
Seagrass Meadows: Underestimated Champions
Shallow-water seagrass beds provide underappreciated coastal protection. Their dense vegetation stabilizes seafloor sediments while serving as nurseries for commercially valuable fish species. These meadows contribute significantly to marine biodiversity and food security.
Like wetlands, seagrasses excel at carbon sequestration. Their submerged soils store carbon for centuries when undisturbed. Incorporating seagrass conservation into coastal management plans offers a cost-effective climate adaptation strategy with multiple co-benefits.
Integrated Coastal Zone Management: A Holistic Approach
Effective coastal adaptation requires systems thinking. ICZM frameworks harmonize ecosystem conservation with human development needs. This approach acknowledges that coastal protection, economic activity, and community wellbeing are interdependent.
Successful ICZM implementation demands cross-sector collaboration. By aligning policies across government agencies, businesses, and communities, coastal managers create resilient systems that withstand environmental pressures. Adaptive management principles ensure strategies evolve with changing conditions and new scientific insights.
Strategic planning always begins with precise objectives. Clear goals provide the necessary focus to navigate complex projects efficiently. Vague aspirations lead to wasted effort, while specific targets enable measurable progress and optimal resource use.
Integrated Coastal Zone Management: A Holistic Approach

Understanding the Concept
ICZM represents a paradigm shift in coastal governance. This methodology recognizes that human activities and natural systems constantly interact along coastlines. Rather than treating development and conservation as competing priorities, ICZM seeks synergies between them.
The most successful ICZM initiatives actively involve all affected stakeholders. Fishermen, tourism operators, conservationists, and policymakers each contribute unique perspectives that enrich planning processes.
Key Principles of ICZM
ICZM operates on several foundational principles. The ecosystem approach considers how land, water, and atmospheric systems interconnect. Adaptive management allows for course corrections based on monitoring data and changing conditions.
Intergenerational equity ensures current decisions don't compromise future generations' coastal resources. This long-term perspective distinguishes ICZM from short-sighted development models.
Goals and Objectives
ICZM aims to balance ecological health with human prosperity. Typical objectives include habitat restoration, pollution reduction, and sustainable economic development. These goals adapt to local conditions, reflecting unique cultural and environmental contexts.
Effective ICZM programs establish measurable indicators for each objective. Water clarity measurements, species population counts, and economic metrics all help track progress toward coastal sustainability.
Challenges in Implementation
ICZM faces numerous implementation hurdles. Jurisdictional overlaps often create governance complexities, while limited funding constrains long-term planning. Differing stakeholder priorities can stall decision-making processes.
Successful ICZM requires institutional mechanisms to resolve conflicts and align diverse interests. Neutral facilitation and science-based mediation often prove essential for overcoming impasses.
Stakeholder Involvement and Participation
Authentic stakeholder engagement distinguishes token consultation from meaningful participation. Coastal communities possess generations of place-based knowledge that complements scientific data.
Inclusive processes build ownership and improve compliance with management measures. When residents help shape solutions, they become active partners in implementation rather than passive recipients of policies.
Monitoring and Evaluation
Continuous monitoring provides the feedback loop essential for adaptive management. Environmental indicators track ecosystem health while socioeconomic metrics gauge community impacts.
Regular program reviews ensure ICZM plans remain responsive to new challenges and opportunities. This iterative approach allows coastal managers to incorporate emerging best practices and technological advancements.
Read more about Sea Level Rise Adaptation for Coastal Development
Hot Recommendations
- AI in Property Marketing: Virtual Tours and VR
- Water Management Solutions for Sustainable Real Estate
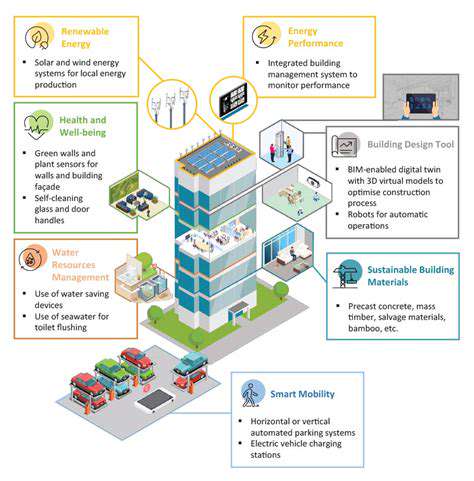
- IoT Solutions for Smart Building Energy Management
- Sustainable Real Estate: Building a Greener Tomorrow
- Sustainable Real Estate: From Concept to Community
- AI Driven Due Diligence for Large Scale Developments
- Real Estate Sector and Global Climate Agreements
- Smart Buildings: The Key to Smarter Property Management
- Zero Waste Buildings: A Sustainable Real Estate Goal
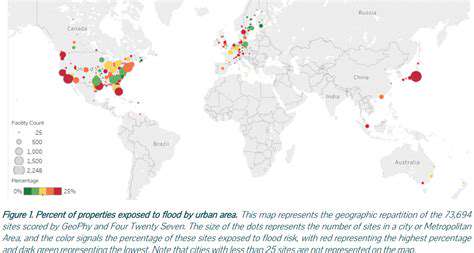
- Understanding Climate Risk in Real Estate Financing